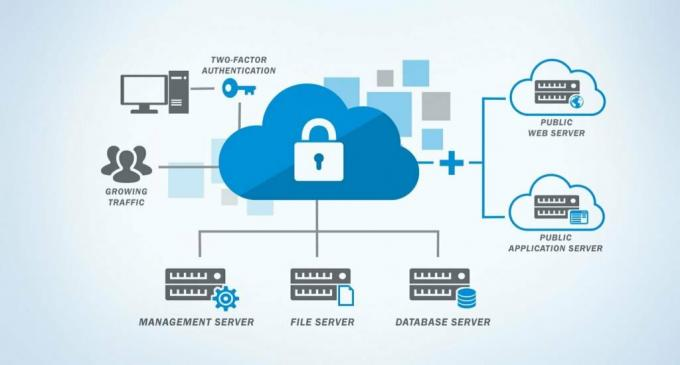
Since the pandemic, digital has become part of the company’s daily life. This transformation engenders vigilance that should not be neglected.
Digital transformation and cloud adoption have accelerated further as a result of the Covid-19 pandemic. Small businesses have started selling more products and services from websites, and businesses have started moving more workloads to the cloud to facilitate remote work and innovate. Ultimately, digital transformation and cloud computing strategies bring productivity, profitability, innovation and growth to businesses. Safety practitioners need to enable these transformations more safely.
While taking advantage of these opportunities is undoubtedly a net benefit for businesses of all sizes, digital transformation projects are prone to misconfiguration and pose new (cloud) security monitoring challenges. A “compromised” mindset prepares security teams for the inevitable changes and risks resulting from the transformation of business processes.
Can security practices evolve as the business grows to automate and digitize, resulting in greater agility and visibility in IT environments, from the on-premises to the cloud? Turn to a safer future with advanced detection and response.
Today, ransomware operations focus on data exfiltration before encrypting sensitive files and critical systems. With regard to technology and processes, it is clear that preventive controls are in place for most companies, but they are not sufficient.
Greater visibility through advanced detection and response capabilities helps align with the “assumed compromise” mentality and stop the most dangerous ransomware attacks. Cloud infrastructure provides the ability to scale and automate security processes.
There are countless examples of ransomware attacks in which bypassing initial perimeter controls allowed opponents to gain unlimited access to corporate resources. As a result, being inside the company’s network is no longer a reason to trust a user or device. Requiring authentication each time a user or device requests access to different resources mitigates the problem of implicit trust of users or devices. Still, we must remain alert to the risks.
BRAMS Partnership with the leader
With its expertise, BRAMS offers you market-leading cloud solutions billed per use. With BRAMS, now you can unleash your full potential and focus on what matters most: Your activities with maximum security for your system. Thanks to its partnerships and collaboration with the biggest global cloud pioneers: Microsoft, Amazon Web Services, IBM Cloud and Google Cloud, Brams has become a multi-industry focus, to support companies of different sectors and sizes to move to the Cloud for more than two decades of expertise.
Get in touch with an Expert ..
Source: https://www.globalsecuritymag.fr/Securiser-la-transformation,20220324,123535.html