The answer is, it depends.
Is the public cloud more secure or less secure? This seems to be a matter of hot debate in the industry. There are many examples where, with standardized and comprehensive monitoring and support, the choice to move an application to cloud can make that application fundamentally more secure than before. This is because a cloud vendor is likely to have very robust policies and procedures in place, along with the talent pool to deliver high-grade security. But there are also plenty of examples where IT teams — for specific crown-jewel datasets like customer information or trade secrets — prefer to keep their security on-premises. This means they can meet their own (or regulated) higher and more specific standards for security and avoid introducing new security risks.
The 2021 IBM Cost of a Data Breach report
In the 17th annual 2021 IBM Cost of a Data Breach report, we set out to uncover insights from over 500+ breaches and 3,500 customers to understand what it was that set apart the companies who had suffered a breach from those who had not. From this, we can share valuable insights and lessons you can apply to your own situation to ensure responsible data stewardship as a business or IT leader.
First, the bad news: A public cloud-based breach is likely to cost 32% more, on average, than a hybrid cloud-based breach:
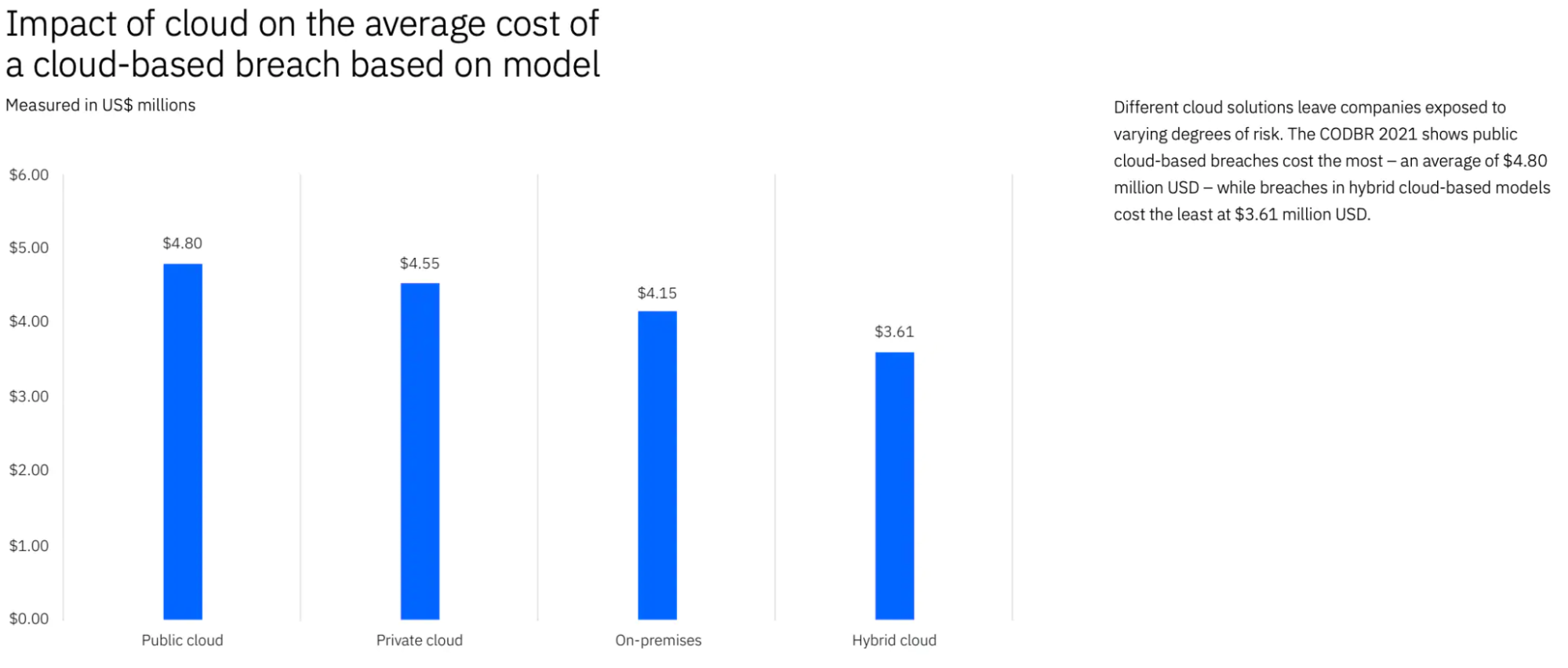
In addition to the public cloud being a more costly breach, it turns out that, based on the initial attack vectors, there are certain types of attacks that are more common in cloud environments than others. The two most common attack vectors for public cloud attacks are compromised credentials and cloud misconfiguration.
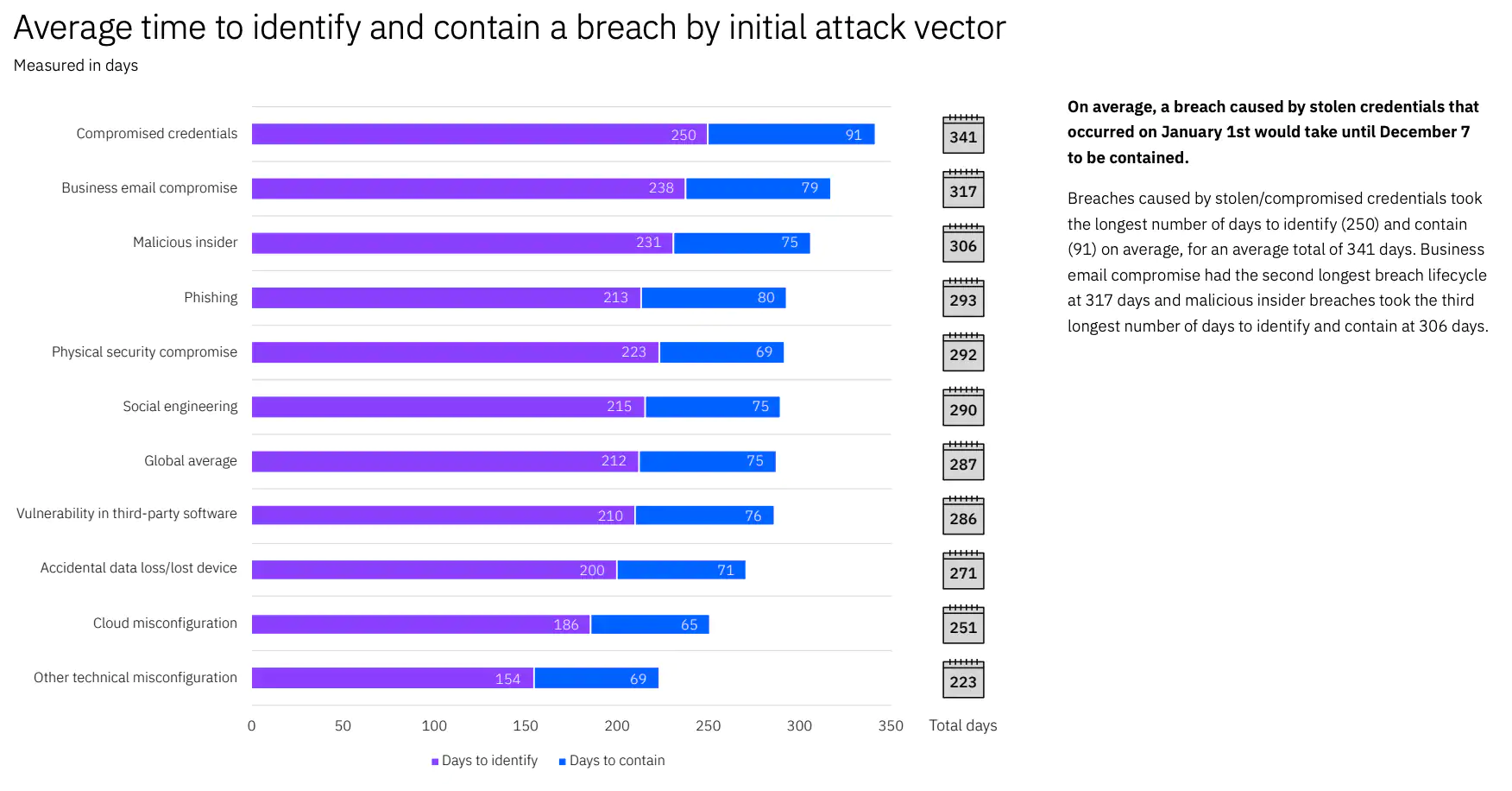
Lastly, like most data breaches, public cloud-based breaches take months — not days or weeks — to correct. While compromised credentials is the attack vector with the longest identify-and-contain time at 341 days — almost an entire calendar year — that is only 16% more than the global average across all attack vectors, which currently stands at 287 days:
So, with all of this said, if you’ve got a cloud environment and any of this is keeping you up at night, I’m guessing you’re going to want to address these things immediately, correct? In the first blog post of this three-part series, IBM Cloud CTO for Security Raj Nagaratnam covered five ways to address cloud security — specifically exploring cloud misconfigurations and compromised credentials. You’ll also want to check out the second blog, written by IBM Cloud CTO Hillery Hunter, on confidential computing. This technology uses hardware-based protection for data in-use to create renewed levels of privacy assurance for cloud-based datasets and combat the problem of compromised credentials.
Mitigating the cost and time to address a cloud data breach
How does all of this help you plan for the future? Let’s learn from the best practices of experts! To mitigate the cost and time to address any cloud data breach, here are three approaches you should be looking into alongside the ones mentioned above:
1. Be particularly cautious during a cloud migration
Whether you are planning a cloud migration to launch a new mobile app or modernize elements of your application estate, the time spent in the planning stage is critical. Migrating to a cloud can be a risky time and, based on our research, is the single biggest factor of whether a cloud data breach occurred at all. Companies with a mature stage of migration experienced shorter windows to identify and contain data breaches. This means that if you are planning to migrate to a cloud environment or if you’re doing so right now, paying extra attention to the number of new users, the number of new tools and processes you might be using and ensuring a sound governance approach is a necessary and solid plan. The average company appears to be using between 26-32 different cloud security tools, just for starters, and more isn’t always the merrier in this case. It might just mean more management.
2. Automate your security and make it more intelligent
Remote working has created more automation over the past few years. Employing security automation and AI tools was associated with a lower average cost of data breach and shorter breach lifecycle. This just makes sense, as security endpoints and data are growing exponentially, while algorithms are becoming better able to find granular issues that typical threshold-based alerting systems might not detect. The 2021 Cost of a Data Breach Report found that organizations with no security AI and automation averaged a hefty cost of 6.71 million USD per breach, whereas an organization with a fully deployed system saw costs averaging 2.90 million USD. The choice of whether to use an AI platform was a leading factor in mitigating costs, with an average cost difference of 1.49 million USD.
3. Take a “zero trust” approach to your cloud stack
Zero trust is an industry framework for managing security in different domains including the network, identity and data. With the recent U.S. executive order calling for it, this is becoming a de-facto standard. The 2021 Cost of a Data Breach Report found that a zero trust approach helped reduce the average cost of a data breach by 1.76 million USD, representing a difference of 42.3%.
While the selection and roll-out of such a framework tends to begin in the Chief Information Security Officer’s group, the typical cloud solution architect or cloud team should be shifting now towards a technical assurance posture for their cloud, where they no longer allow only policies or operational assurance to dictate what occurs. Technologies like confidential computing, as part of a zero trust approach, remove the implicit trust that applications place in the underlying software stack and cloud providers, allowing you to modernize operations and embed security into each step of the development cycle to help reduce the cost and impact of a data breach.
Moving toward a cloud without compromise on security
IBM offers the most secure infrastructure operations on the planet. Our servers suffer the fewest breaches and have consistently done so year after year, as demonstrated by the annual ITIC Global Hardware, Server Reliability and Security report. Those same servers are embedded in the IBM Cloud with IBM Cloud Hyper Protect Services, which have helped IBM clients to design in privacy with the industry’s first and only FIPS 140-2 Level 4 certified cloud hardware security module (HSM) [1]. To our knowledge, the IBM Cloud suffered no successful data breaches in 2020.
[1] The Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. government computer security standard used to approve cryptographic modules. It is issued by the National Institute of Standards and Technology (NIST). Level 4 is the highest level of security.
Brams & IBM Cloud a winning partnership
Collaborating with a IBM Cloud partner like Brams gives you the best of the expertise , you’ll get the best of the expertise for a swift migration and effective optimisation, collaborate with a dedicated account manager who will conduct account reviews and regularly identify opportunities for cost and performance optimization and also you’ll get support and monitoring responses

Get In Touch With An Expert:
Source: https://www.ibm.com/cloud/blog/is-the-cloud-more-secure-or-less-secure