Cloud Run makes developing and deploying containerized applications easier for developers. At the same time, Cloud Run services need to be secure. Today, we’re announcing several new ways for you to secure your Cloud Run environments:
- Mount secrets from Google Secret Manager
- Use Binary Authorization to ensure you only deploy trusted container images
- Use your own encryptions keys
- Get recommendations based on the principle of least privilege
Let’s take a closer look at each of these new features.
1. Mount secrets from Google Secret Manager
You might have previously stored API keys, passwords, certificates, and other sensitive data in environment variables. This is not considered a best practice. More security-conscious customers store sensitive data in Secret Manager, Google Cloud’s secure system for storing API keys, passwords, certificates, and other sensitive data. However, accessing these secrets from a Cloud Run service traditionally requires developers to use client libraries.
Now, you can mount secrets from Secret Manager as environment variables or file system volumes in your Cloud Run services, from the command line:
or from the Google Cloud Console:
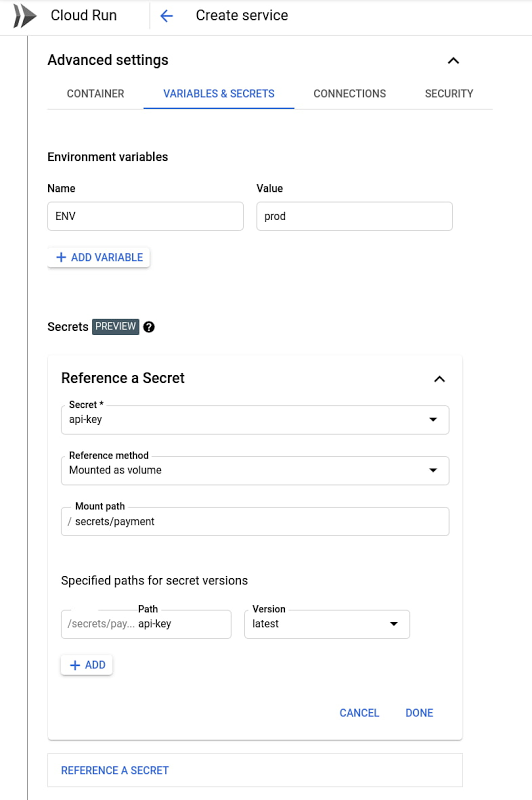
Secret Manager features fine-grained IAM permissions: By default, Cloud Run services do not have the permission to access Secret Manager secrets; access must be specifically granted. Integration with Secret Manager also allows you to encrypt secrets with your own encryption keys.
Learn more about Cloud Run integration with Secret Manager in this video:
2. Binary Authorization for Cloud Run
Containers are the industry-standard way to package and run software. Cloud Run enables developers to deploy and scale containers in a fully-managed environment. Today, we’re introducing Cloud Run integration with Binary Authorization.
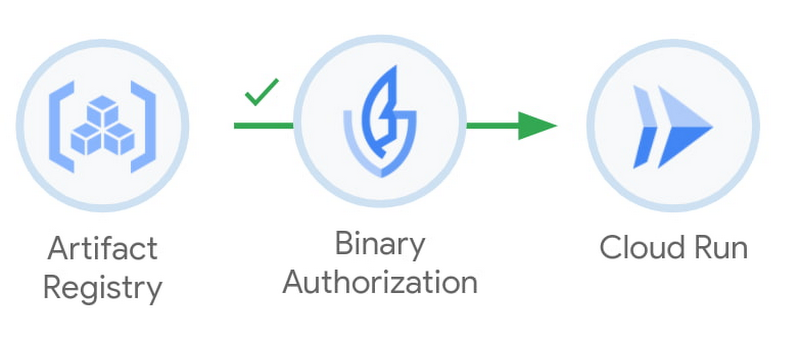
With Binary Authorization, security administrators can now define and enforce policies about the containers that are being deployed to Cloud Run. For example, organization administrators can enforce that Binary Authorization be used on Cloud Run services in a certain project. This process is transparent to developers, who can deploy to Cloud Run as usual, being sure that the container will meet any defined policies.
With Binary Authorization and Cloud Run, you can enforce that a container:
- was created using an approved build system
- was approved by the QA team
- was analyzed for vulnerabilities
Mike Helmick, Principal Software Engineer, COVID-19 Exposure Notifications, uses Binary Authorization alongside Cloud Run, which he credits for improving their compliance posture:
“As part of our efforts to combat COVID-19, Google built the exposure notifications key and verification servers. We leverage Binary Authorization for Cloud Run to ensure that the servers are always built with our trusted Cloud Build builders, give us an audit trail, and ensure that the code that is running is what we intend.”
3. Customer-managed encryption keys
By default, container images deployed to Cloud Run are encrypted at rest with Google-managed encryption keys. Customers with higher security needs might want more control over the encryption of their resources at rest to improve their confidence in using the public cloud. A container image is such a resource.
Rolling out over the next few days, we are introducing a preview of customer-managed encryption keys for Cloud Run. This capability allows you to protect container images using encryption keys that you manage within Cloud Key Management Service, or KMS.
The keys in Cloud KMS are called customer-managed encryption keys (CMEK). When you protect data in Cloud Run with CMEK, the CMEK key is within your control, not controlled by Google. This means that when these keys are disabled or destroyed, no one (including Google) can access the data protected by these encryption keys, putting protection in your control.
Support for CMEK in Cloud Run is particularly important for regulated industries such as financial services. Just as Artifact Registry uses CMEK to protect the storage of container images, Cloud Run’s support of CMEK extends this protection to container images that are deployed into production, protecting the container across the build, deploy and run process.
You can get started with Binary Authorization or customer-managed encryption keys from the command line or the Cloud Console:
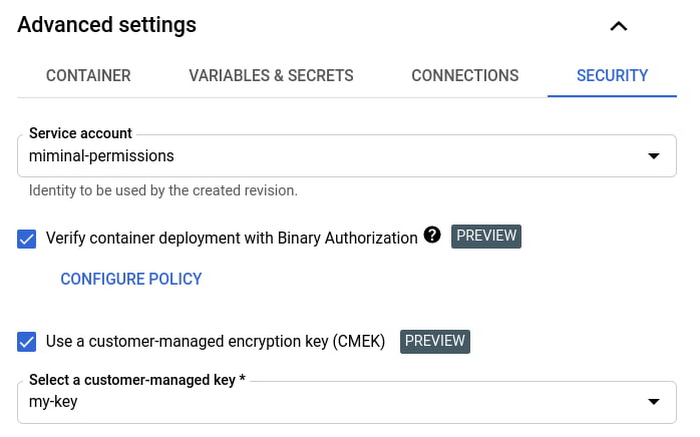
Further, you can enforce the use of Binary Authorization or Customer-managed encryption keys on all Cloud Run services in your projects using an Organization Policy constraint.
4. Get recommended best practices
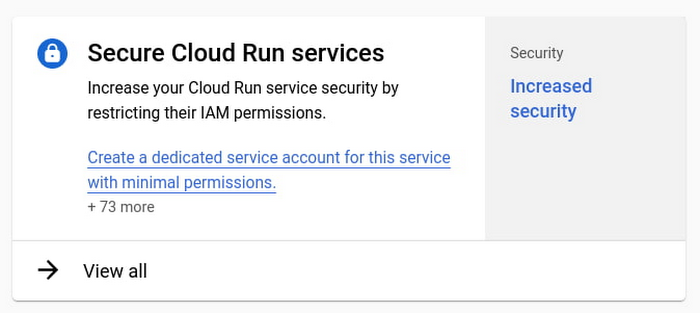
By default, Cloud Run services run with the same identity as Compute Engine VMs: the default Compute Service Account. This is a great way to get started quickly and without bothering with permissions. At the same time, it’s a best practice to only give to your Cloud Run service the permissions it needs to operate.
Starting today, you will see recommendations in Recommendation Hub to create dedicated service accounts for your Cloud Run services with minimal sets of permissions. Look for a blue light bulb icon in the Cloud Run user interface. Or, you can find recommendations to improve the security of your Cloud Run services in the Recommendations tab of the Cloud Console home page:
BRAMS Partnership with the leader
With its expertise, BRAMS offers you market-leading cloud solutions billed per use. With BRAMS, now you can unleash your full potential and focus on what matters most: Your job. Thanks to its partnerships and collaboration with the biggest global cloud pioneers: Microsoft, Amazon Web Services, IBM Cloud and Google Cloud, Brams has become a multi-industry focus, to support companies of different sectors and sizes to move to the Cloud for more than two decades of expertise.
Get In Touch With An Expert
Source : https://cloud.google.com/blog/products/serverless/improving-the-security-of-your-cloud-run-environment

